Token update notifications
Configure a webhook to receive Network Token update notifications.
Use this service to get notified whenever something on the Network Token or it's underlying PAN changes. It pushes an HTTP message to a webhook of your choice and updates the card data mapped to the alias value stored in your token vault.
More specifically, a Token status request will be sent whereas the following parameters will be updated as soon as the respective card network triggers a change.
{
"alias": "7LHXscqwAAEAAAGQl2DPXQbbUOZ4ADnU",
"fingerprint": "F-cg_iu0Xulk1UNMtL57hZW3",
"type": "CARD",
"masked": "22228502xxxx7008",
"dateCreated": "2024-07-09T12:03:42Z",
"card": {
"usage": "REGISTRATION",
"panRemoved": false,
"bin": "22228502",
"last4": "7008",
"expiryMonth": "12",
"expiryYear": "30",
"cardInfo": {
"brand": "MASTERCARD",
"type": "credit",
"usage": "consumer",
"country": "US",
"issuer": "",
"accountType": "PAN"
},
"networkToken": {
"expiryMonth": "08",
"expiryYear": "27",
"status": "ACTIVE",
"paymentAccountReference": "5001CKVAXG3BF45LG87F63JVX3AQ0",
"tokenRequestorId": "50179002095",
"token": "2222850249926011"
}
}
}| Parameter | Description |
|---|---|
masked | Masked number of underlying PAN. Keeps original length of the card. |
last4 | The last four digits of the underlying PAN. |
card.expiryMonth | The expiry month of the underlying PAN. |
card.expiryYear | The expiry year of the underlying PAN. |
networkToken.status | The status of the underlying PAN. |
paymentAccountReference | The payment account reference number of the underlying PAN. |
networkToken.expiryMonth | The expiry month of a Network Token. |
networkToken.expiryYear | The expiry year of a Network Token. |
maskedcard numberDue to limitation on the scheme APIs, we can only update the masked card number for Visa and Mastercard.
We recommend using the
last4property for identification purposes in customer profiles, as it will be updated for all available brands
Please contact us if you are missing a parameter.
Activation
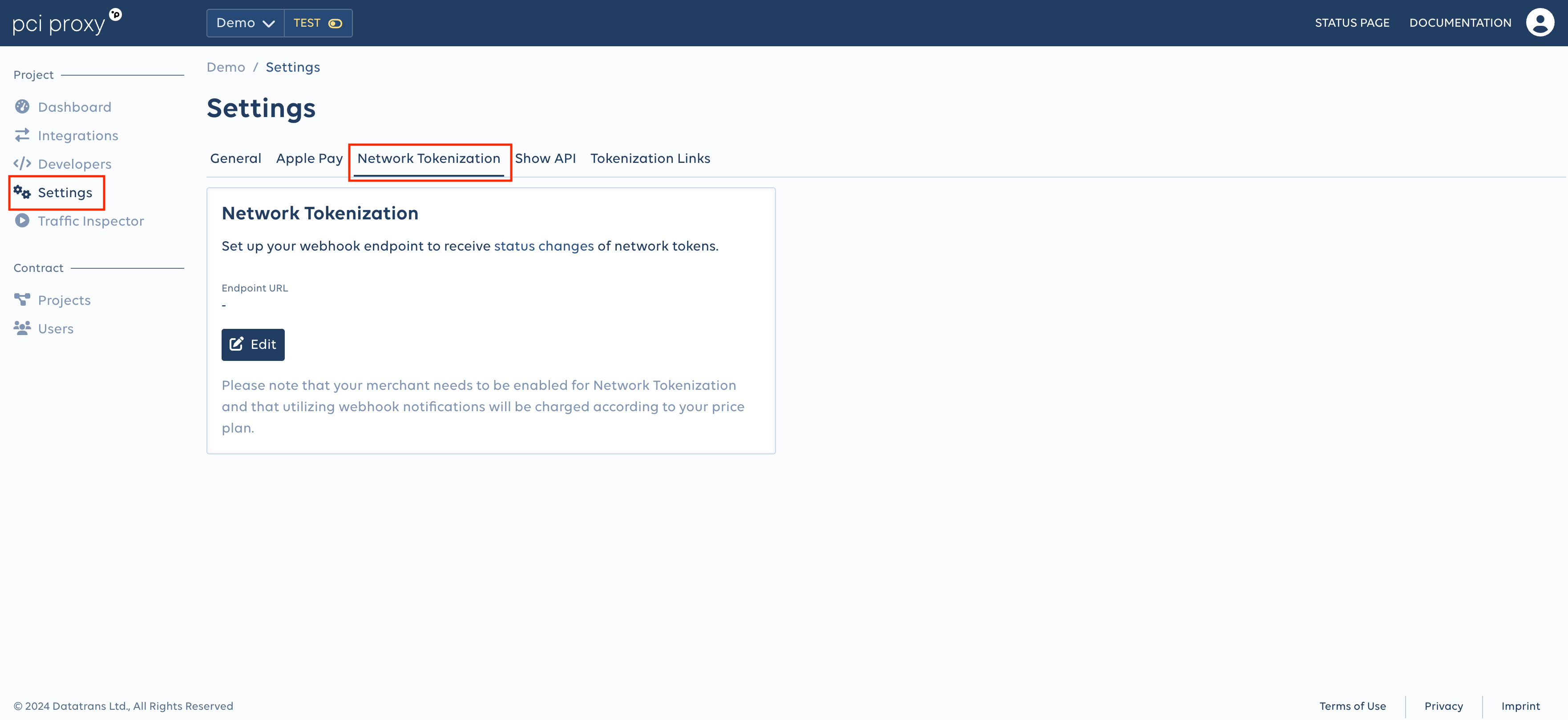
To enable Network Token update notifications and to configure your webhook please login to your account. Navigate to the Network Tokenization section tab within the Settings menu on your project and add the endpoint url.
Additional security - webhook signing
To protect our webhooks from being tampered, add an additional security layer by signing our webhooks. To access your HMAC key, login to our dashboard and navigate to the API Keys tab in the Developers menu within the project section and look for the Webhook Sign Key value. PCI Proxy will use this key to calculate a signature and add two parameters within the HTTP request header request-signature: A unique timestamp t and the expected signature s0.
To calculate the expected signature, concatenate the timestamp as a string with the webhook payload. Convert the resulting string to bytes and finally create a signature with your HMAC key using SHA256. Finally, compare your calculation to the expected signature s0. If your calculated signature equals s0, the webhook payload is valid and was not modified.
// hex bytes of the key
byte[] key = Hex.decodeHex(key);
// Create sign with timestamp and payload
String algorithm = "HmacSha256";
SecretKeySpec macKey = new SecretKeySpec(key, algorithm);
Mac mac = Mac.getInstance(algorithm);
mac.init(macKey);
mac.update(String.valueOf(timestamp).getBytes());
byte[] result = mac.doFinal(payload.getBytes());
String sign = Hex.encodeHexString(result);# hey bytes of the key
key_hex_bytes = bytes.fromhex(key)
# Create sign with timestamp and payload
sign = hmac.new(key_hex_bytes, bytes(str(timestamp) + payload, 'utf-8'), hashlib.sha256)# Create sign with timestamp and payload
echo hash_hmac('sha256', $timestamp . $payload, hex2bin($key));To verify if you calculated the signature in the right way, the example below can be used. When testing locally, beware of pretty formatting the webhook payload, as it will result in a different signature than expected.
Given the key:
861bbfc01e089259091927d6ad7f71c8b46b7ee13499574e83c633b74cdc29e3b7e262e41318c8425c520f146986675fdd58a4531a01c99f06da378fdab0414a
Given the payload:
HELLO
Given the timestamp:
1605697463367
Then the signature is:
t=1605697463367,s0=82ef9a8178dcb4df0b71540fa06d7da826ecb26e1977e230bdc8c9d6f9f1af84Retries
Retries are done max. 10 times with an exponential backoff until we receive an HTTP 2xx status code.
Updated 4 months ago